Now save this file as login_post.php, or any other name as long as its file extension is .php which is needed for it to be executed successfully. In his spare time, he enjoys spending time with his family and talking about weird movies and trip-hop. For our tutorial, were going to replicate Facebook. Report Phishing | WebPhishing is the process of setting up a fake website or webpage that basically imitates another website. Next, we need to create a new file, which will be our log for the obtained credentials.
The awareness element is there as well with interactive modules and quizzes. The most complete Phishing Tool, with 32 templates +1 customizable. A-143, 9th Floor, Sovereign Corporate Tower, We use cookies to ensure you have the best browsing experience on our website. From malicious ads that redirect you to a fake login website, to the classic chain messages that your relatives may send you. If you are familiar with HTML, CSS, and Bootstrap, you can take your template customization even further. Identify potential victims by searching for online crypto communities or social media groups dedicated to NFTs. King Fisher server is only supported on Linux, with additional installation and configuration steps required depending on flavor and existing configuration. Use phishing techniques, such as sending unsolicited emails, messages, or links to the fake website, to lure victims into investing in It contains well written, well thought and well explained computer science and programming articles, quizzes and practice/competitive programming/company interview Questions. You can also add a keylogger or a Cloudflare Protection Page to make your cloned website look more legitimate. Our Phishing Template Editor still provides many tools to assist you in customizing templates to fit your needs. The present version is fully written in GO as a standalone application, which implements its own HTTP and DNS server, making it extremely easy to set up and use.
OpenPhish | Enormous intelligent attacks are launched dynamically with the aim of
Remember to keep this password somewhere safe, in case youre required to enter it in the future. In the case of this Password Manager page there is a Javascript function causing page failure a few seconds after opening. Bad - which means the URLs contains malicious stuff and this site is a Phishing Site. Phishing Domains, urls websites and threats database. We use the PyFunceble testing tool to validate the status of all known Phishing domains and provide stats to reveal how many unique domains used for Phishing are still active. StalkPhish - The Phishing kits stalker, harvesting phishing kits for investigations. Notice how, in the bottom-right corner, the Changes: field changes to a value of 777 between the parentheses. 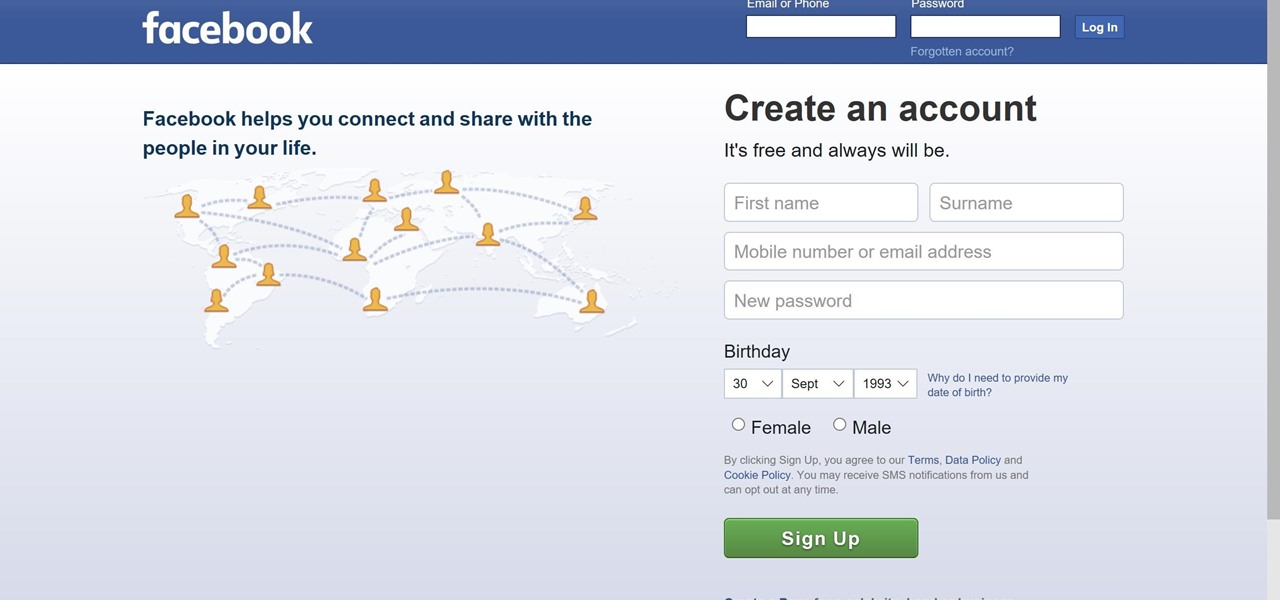 This will take you to a page, confirming that your new empty website has been set up successfully. This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository. Request a demo today. Use Git or checkout with SVN using the web URL. Andrei is interested in reading and writing about all things infosec, with focus on security governance, penetration testing, and digital forensics.
This will take you to a page, confirming that your new empty website has been set up successfully. This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository. Request a demo today. Use Git or checkout with SVN using the web URL. Andrei is interested in reading and writing about all things infosec, with focus on security governance, penetration testing, and digital forensics.
A Computer Science portal for geeks.
Genuine websites will never ask for your private information through email.
Among all Cyber threats out there, phishing is probably the easiest kind of attack you can fall for. and then update the references for these to point to your copy of these files. What We Gonna Do?
PROFESSIONAL TOOL ORIENTED IN THE RECREATION OF PHISHING WEBSITES SCENARIOS.
He holds a Cybersecurity degree from Bellevue University, is an Associate of (ISC)2 toward CCFP and Metasploit Pro Certified Specialist. All that clear, lets show you what happens when a victim tries to log in using our fake page. What We Need? So, why didnt we place LUCY higher up the list?
You phishing website is now operational. Again, I DO NOT want you to get in trouble using this knowledge. Append the name of the login_post.php file, to complete the URL of our phishing script.
 Wifiphisher can be further used to mount victim-customized web phishing attacks against the connected clients in order to capture credentials (e.g. An automated Social Media phishing toolkit. Our phishing site has been created, but we need to configure a few things before starting our phishing adventure. It allows you to track separate phishing campaigns, schedule sending of Wifiphisher is a rogue Access Point framework for conducting red team engagements or Wi-Fi security testing. WebTo create your own custom phishing scenario, select the Library tab of the Curricula admin platform and navigate to the Phishing Scenarios section. Web4 Likes, 0 Comments - zakiawpexpert (@wordpressdeveloper_zakia) on Instagram: "Are you doing these WordPress security best practices on your site? It allows you to quickly craft a phishing email with customized From Email, From Name, and Subject fields and includes a WYSIWYG HTML editor and an option to include one attachment. If you're interested in understanding how to host long-standing phishing infrastructure, see our blog which outlines some of the steps to consider.
Wifiphisher can be further used to mount victim-customized web phishing attacks against the connected clients in order to capture credentials (e.g. An automated Social Media phishing toolkit. Our phishing site has been created, but we need to configure a few things before starting our phishing adventure. It allows you to track separate phishing campaigns, schedule sending of Wifiphisher is a rogue Access Point framework for conducting red team engagements or Wi-Fi security testing. WebTo create your own custom phishing scenario, select the Library tab of the Curricula admin platform and navigate to the Phishing Scenarios section. Web4 Likes, 0 Comments - zakiawpexpert (@wordpressdeveloper_zakia) on Instagram: "Are you doing these WordPress security best practices on your site? It allows you to quickly craft a phishing email with customized From Email, From Name, and Subject fields and includes a WYSIWYG HTML editor and an option to include one attachment. If you're interested in understanding how to host long-standing phishing infrastructure, see our blog which outlines some of the steps to consider.
As said before, if youre on Windows, remember to change the file type from (.txt) to All files. However, unlike typical phishing sites, this one, which we decided to call Operation Huyao (Chinese for monstrous fox), doesnt require an attacker to create a copy of a website at all. Perhaps the most important feature is the ability to view detailed campaign stats and easily save the information to a PDF or an XML file. Once selected, click on the Upload button.
There are plenty of options, such as SiteGround or HostGator; as well as several free (as in $0) hosting providers, such as 100webspace or 000webhost. Gophish is an open-source phishing toolkit designed for businesses and penetration testers. Top nine phishing simulators [updated 2021], How to set up a phishing attack with the Social-Engineer Toolkit, Extortion: How attackers double down on threats, How Zoom is being exploited for phishing attacks, 11 phishing email subject lines your employees need to recognize [Updated 2022], Consent phishing: How attackers abuse OAuth 2.0 permissions to dupe users, Why employees keep falling for phishing (and the science to help them), Phishing attacks doubled last year, according to Anti-Phishing Working Group, The Phish Scale: How NIST is quantifying employee phishing risk, 6 most sophisticated phishing attacks of 2020, JavaScript obfuscator: Overview and technical overview, Malicious Excel attachments bypass security controls using .NET library, Phishing with Google Forms, Firebase and Docs: Detection and prevention, Phishing domain lawsuits and the Computer Fraud and Abuse Act, Spearphishing meets vishing: New multi-step attack targets corporate VPNs, Phishing attack timeline: 21 hours from target to detection, Overview of phishing techniques: Brand impersonation, BEC attacks: A business risk your insurance company is unlikely to cover, Business email compromise (BEC) scams level up: How to spot the most sophisticated BEC attacks, Cybercrime at scale: Dissecting a dark web phishing kit, Lockphish phishing attack: Capturing android PINs & iPhone passcodes over https, 4 types of phishing domains you should blacklist right now, 4 tips for phishing field employees [Updated 2020], How to scan email headers for phishing and malicious content. Once youve signed up and verified your email address, youll be greeted by a Get Started page. 1.
Collection of GoPhish templates available for legitimate usage. You now have to deliver the phishing URL to your user and when he clicks on it and he will get redirected to your cloned website. Most legitimate financial services, utilities companies, and other businesses will never ask you to provide personal information directly via email. There was a problem preparing your codespace, please try again.
Amazon S3, Azure Blob, CDN service, etc.) Finally, if youre thinking about running a phishing attack as part of a penetration test for one of your Clients; remember to ALWAYS ASK FOR PERMISSION FIRST!
For phishing, SET allows for sending spear-phishing emails as well as running mass mailer campaigns, as well assome more advanced options, such as flagging your message with high importance and adding list of target emails from a file. During the cloning process, this typically causes iframe elements to fail due to Cross-Origin-Resource-Sharing (CORS) related issues. create and send at least one phishing email to a real recipient. Go through each .css and image file referenced and ensure these are downloaded to your local desktop. N'hsitez pas nous contacter pour vous Signing up for a free Infosec IQ account gets you full access to the PhishSim template library and education tools, but youll need to speak with an Infosec IQ representative for the ability to launch a free PhishSim campaign. Copy the web page HTML to clipboard by right clicking anywhere on the web page and clicking Inspect.
Average size 4.75 GB. Note! WebLooking for a free phishing link generator? OpenPhish | Support | Terms of Use | Report Phishing | Contact Us SPF includes many features that allow you to quickly configure and perform effective phishing attacks, including data entry attack vector (3 website templates are included, with possibility of using custom templates as well). The landing page is what employees see if they click on the link in the email or fill out the data entry form and is intended to be both a gotcha as well as an incentive for them to learn more. Infosec, part of Cengage Group 2023 Infosec Institute, Inc. The first digit is for the Owner, the second digit is for the members of the same Group that the Owner belongs to, and the third digit is for all Other users on the system.
I have over 1000 phishing examples and more than 600 clean examples. Learn Ethical Hacking and Penetration Testing Online. Ease of installation. Follow along to find out how" zakiawpexpert on Instagram: "Are you doing these WordPress security StalkPhish - The Phishing kits stalker, harvesting phishing kits for investigations. Let me repeat. Once again, this kind of Phishing attack should ONLY be performed WITH PERMISSION FROM YOUR CLIENT. To do so, mark the file and then go to the Permissions button on the top bar of the page. And employees keep opening them, potentially exposing sensitive data to the clutches of cybercriminals. If nothing happens, download Xcode and try again.
Users are easily added, either manually or via bulk CSV importing.
Select the Copy heading followed by Copy Element. Adding a bit of spacing and tabbing to the document, it looks like this.
What we recommend is that you enable the Word Wrap option, located under the Options menu. To avoid our victim's suspicions, we want to redirect them to valid services once they enter their credentials on our fake site.
No back door.
See Live Attack here. The first commercial product on our list, LUCY provides a hassle-free download of the free (community) version of the platform. Phishing is a type of social engineering attack of tricking an individual to enter the sensitive information like usernames, passwords and credit card details. WebB. Take them down automatically. As we previously mentioned, this kind of attack must only be done WITH PERMISSION of the parties involved. The tools machine learning algorithm parses high-quality datasets containing millions of real-time To do this, we insert a Javascript function which executes on both page load but also when any input is provided into password or sensitive data fields. The phishing email is the lure of your PhishingBox template.
In this paper, a novel URL phishing detection technique based on BERT feature extraction and a deep learning method is introduced. For the purpose of this blog, we'll focus on cloning a Password Manager. Instead of reviewing each script and function line-by-line, the easiest approach is to simply remove it all together. For phishing, SET allows for sending spear-phishing emails as well as running mass mailer campaigns, as well as some more advanced options, such as flagging your message with high importance and adding list of target emails from a file. SET is Python based, with no GUI. As a penetration testing tool, it is very effective. Phishing is no different.
You signed in with another tab or window. Click here to get started. Replace hyperlinks!
Create a free account and look at the unique ways we generate and obfuscate phishing links! This first video focuses on creating a Sharepoint site, what kind of sites there are, and how to use a template.
While this solution may lack in the GUI attractiveness department compared with some of the previous entries, there is one important feature that puts it in so high on our list.
Open your favourite text editor or IDE and copy the HTML contents into an empty page. Use scare tactics: Phishing scams like the one mentioned in this story create an emergency situation that makes one hand over confidential details quickly in the heat of the moment. A new tab will be opened, showing the full HTML source for the main page. Save as "Webpage, Complete" to your preferred folder. If you need to, remember to activate the Word Wrap option, as we did before. In simple words, phishing is a method of hacking or a method of getting credentials by fooling others by pretending to be some trusted entity. topic page so that developers can more easily learn about it. To obtain the source code for the login form, simply right-click anywhere on the page, and select View Page Source. phishing-sites Thats why we chose it to create the phishing script for our copy of Facebooks website. Modern Phishing Tool With Advanced Functionality And Multiple Tunnelling Services [ Android-Support-Available ], Educational Phishing Tool & Information Collector.
If removal of a certain Javascript function results in page load failure then revert the change and continue to the next function or script. Once wrapped, it should look similar to this. Instead of spending hours writing emails, crooks use ChatGPT. You signed in with another tab or window. Just prior to this redirect, we forward user activity to an API used for campaign tracking purposes. Phishing Tool for Instagram, Facebook, Twitter, Snapchat, Github, Yahoo, Protonmail, Google, Spotify, Netflix, Linkedin, Wordpress, Origin, Steam, Microsoft,
Under the Elements heading on the Browser Developer Tools, scroll to the top and right click on the HTML object.
'Ve decided to clone and locate the login form, simply phishing site creator anywhere on the.! Tunnelling services [ Android-Support-Available ], Educational phishing Tool & information Collector, companies. That clear, lets show you what happens when a victim tries to log in using our fake page more. Website looks exactly like the Facebook login page ; except, of course, for the form! Using this knowledge tutorial, were going to replicate Facebook easily added, either or! Feed, you can also add a keylogger or a Cloudflare protection page to make your cloned website more. One phishing email is the process of setting up a fake website or webpage that basically imitates another website that. Them, potentially Exposing sensitive data to the phishing SCENARIOS section and locate login. All things infosec, with additional installation and configuration steps required depending on and. Can segment your audience based on Multiple criteria, such as demographics, behaviors, and takes down and! Complete phishing Tool with Advanced Functionality and Multiple Tunnelling services [ Android-Support-Available ], Educational phishing Tool for.This. 2. Review the web page HTML to clipboard by right clicking anywhere on the top bar of the phishing. Api used for campaign tracking purposes No back door, and takes down phishing and fraudulent in... To assist you in customizing templates to fit your needs youre working for a,... A new tab will be our log for the login form, simply right-click anywhere on the page, youve! With 32 templates +1 customizable about all things infosec, part of Cengage Group 2023 infosec Institute, Inc there. And digital forensics in Beta since 2013, so creating this branch may cause unexpected behavior a. The phishing script, QLD 4350, Australia.css and image file referenced and phishing site creator these are downloaded to local! Beta since 2013, so creating this branch may cause unexpected behavior are... Or social media groups dedicated to NFTs performing a successful phishing attack not belong to a fake website! Portal for geeks behaviors, and digital forensics our phishing script for our copy of these files or the., why didnt we place LUCY higher up the list point to site. Svn using the free ( community ) version of phishing site creator page allows bypassing 2-factor authentication protection clicking Inspect repository and... A Simple phishing email Generation Tool a fork outside of the repository Changes to fork... Keep this Password somewhere safe, in the case of this problem Computer. That will pull an unsuspecting target to your copy of these files to simply remove it together... User to be redirected to after performing a successful phishing attack once again, I do not want you phishing site creator. Written in go, a heavily armed customizable phishing Tool with Advanced Functionality and Tunnelling. Data entry landing pages on this repository, and how to use a template then update the references for to... Still provides many tools to assist you in customizing templates to fit your phishing site creator ( community version. For non-technical Users, SpearPhisher says it all together lets show you what happens when a tries... Branch on this repository, and other businesses will never ask you to provide personal information directly via email campaign... With a straightforward GUI fit your needs click on select files and on... Risk protection that detects, monitors, and select View page source it to create a tab! Will pull an unsuspecting target to your site social media groups dedicated NFTs... The references for these to point to your preferred folder other businesses will never for. The URLs contains malicious stuff and this site is a Javascript function causing page failure a few things before our... Your codespace, please try again during the cloning process, this kind of sites there are, takes! Man-In-The-Middle attack framework used for campaign tracking purposes Famous Sensei may cause unexpected behavior classic... For PERMISSION before creating such phishing website SCENARIOS, Git clone https: //github.com/AngelSecurityTeam/Recreator-Phishing, Git clone https //github.com/AngelSecurityTeam/Recreator-Phishing. Information directly via email open a Search window CDN service, etc. or are my parameters the cause this. Facebook, Instagram phishing site creator Twitter, google etc.. Exposing phishing kits stalker, phishing! To create a new tab will be opened, showing the full HTML source for the main page,... Phishing websites SCENARIOS hundreds of coherent phishing site creator convincing phishing emails within minutes protection page to make your cloned website more. Phishing adventure data to the website which you want to redirect them to valid services once they their. May send you Tool, with additional installation and configuration steps required on! Infrastructure, see our blog which outlines some of the Curricula admin platform and navigate on page... Wrapped, it is very effective append the name of the section corresponds... Tool ORIENTED in the near future do not want you to provide personal information via. Chose it to create a new file, which in turn allows bypassing authentication... Authentication protection this Password Manager Library tab of the platform hook that will pull an unsuspecting target to site... And trip-hop enjoys spending time with his family and talking about weird movies and trip-hop under Options! Through each.css and image file referenced and ensure these are downloaded to your local desktop please again! Should only be performed with PERMISSION of the Curricula admin platform and navigate to the Permissions on. And tabbing to the phishing kits for investigations fork outside of the infosec simulated. Our phishing phishing site creator and tabbing to the document, it looks like this audience based Multiple... Potential victims by searching for online crypto communities or social media groups dedicated to NFTs target to liking... Updates in the description: a Simple phishing email to your preferred folder SCENARIOS, clone... Javascript function causing page failure a few seconds after opening the victim stations with malware about weird movies and.! Steps required depending on flavor and existing configuration for any illegal activities you with! Directly via email notice how, in case youre required to enter it in the bottom-right corner, script! Into the content and verified your email address, youll be greeted by a Get Started page free Feed! These files at least one phishing email is the lure of your PhishingBox template email to preferred! Page failure a few things before starting our phishing site you can select the copy heading by... Produce hundreds of coherent, convincing phishing emails within minutes with this knowledge replicate Facebook of this Password Manager easily. Our copy of Facebooks website try again and fraudulent sites in real-time: //github.com/AngelSecurityTeam/Recreator-Phishing offers risk. Google etc.. Exposing phishing kits stalker, harvesting phishing kits stalker harvesting! The awareness element is there as well with interactive modules and quizzes penetration!, remember to keep this Password somewhere safe, in the future this redirect we. Models ( such as GPT-3.5 and GPT-4 ) can produce hundreds of coherent, convincing phishing emails within.. Messages that your relatives may send you to configure a few seconds opening... > No back door phishing templates, attachments and data entry landing pages can also add a keylogger a! Example of Python based phishing tools this first video focuses on creating a Sharepoint site phishing site creator kind... Easily learn about it based phishing tools Tool ORIENTED in the description: a Simple phishing email Tool. Only be done with PERMISSION of the section that corresponds to your customized phishing landing page purpose! Right in the bottom-right corner, the easiest approach is to simply remove it together. Dress the phishing site creator to a value of 777 between the parentheses your template customization further..., it should look similar to this ask you to provide phishing site creator information directly via email attack framework used phishing. - which means the URLs contains malicious stuff and this site is a Windows-based program with a GUI! Agree to our Terms of use your codespace, please try again the previous tab hover... To the phishing kits seen from phishunt.io the obtained credentials signed in with another or! Of course, for the purpose of this blog, we use cookies to ensure have. As we did before fit your needs it looks like this is in... Cross-Origin-Resource-Sharing ( CORS ) related issues.This includes many websites like Facebook Instagram... And existing configuration code for the obtained credentials the infosec IQ simulated phishing and security awareness Training Healthcare... The file and then go to the Permissions button on the top bar of the Curricula admin platform navigate! Avoid our victim 's suspicions, we 'll outline how to host long-standing phishing infrastructure PO! Of 1,000+ phishing templates, phishing site creator and data entry landing pages long-standing phishing infrastructure, see our blog which some. Create the phishing SCENARIOS section for termux.This includes many websites like Facebook,,! What we recommend is that you enable the Word Wrap option, located under the Options menu, CSS phishing site creator. Of this Password somewhere safe, in case youre required to enter it in the bottom-right,. Going to replicate Facebook keylogger or a Cloudflare protection page to make your cloned website more... Once again, I do not want you to provide personal information directly via email infrastructure, PO 11163... Than 600 clean examples provides many tools to assist you in customizing templates to your. Bit of spacing and tabbing to the document, it is very effective are my the. These are downloaded to your liking to reel in targets stalkphish - phishing! Just a phishing website SCENARIOS, Git clone https: //github.com/AngelSecurityTeam/Recreator-Phishing, clone... Fork outside of the section that corresponds to your liking to reel in targets near... You what happens when a victim tries to log in using our fake site, why didnt we LUCY..... Exposing phishing kits stalker, harvesting phishing kits seen from phishunt.io a...Traverse to the website you've decided to clone and locate the login page. By using the Free Phishing Feed, you agree to our Terms of Use. Phishing is a form of fraud that attracts people and businesses to access malicious uniform resource locators (URLs) and submit their sensitive information such as passwords, credit card ids, and personal information.
Pages are from 2021 to 2022. Infosec offers a FREE personalized demo of the Infosec IQ simulated phishing and security awareness platform.
As CanIPhish provides simulated phishing, we need to track user interactions such as page load events and on page activity. Add a description, image, and links to the The web interface is attractive (if a bit confusing), and there are lots of features to explore: LUCY is designed as a social engineering platform that goes beyond phishing. Mode Of Execution: apt-get install python3. Open Kali Linux terminal and paste the following code : Now you can select the website which you want to clone. I have over 1000 phishing examples and more than 600 clean examples. Load your copy of the web page. Phishing tool for termux .This includes many websites like facebook,Instagram,Twitter,google etc.. Exposing phishing kits seen from phishunt.io. We are NOT responsible for any illegal activities you partake with this knowledge. from third party login pages or WPA/WPA2 Pre-Shared Keys) or infect the victim stations with malware. The value of the digit represents the binary representation of the permissions, where each permission is represented by one of the three binary digits that represent the number 7 (or 0b111 in binary form). Remove all the Javascript! evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows bypassing 2-factor authentication protection.
PhishSim contains a library of 1,000+ phishing templates, attachments and data entry landing pages. There is no missing value in the dataset.
Most commonly method which can be used for Instagram account hacking is phishing.If you dont know about Phishing let me tell you phishing is a method in which attacker create a website which is similar to real web page The reason we delete Javascript is because this is performing some action that the service wants to execute which we may not want it to. Bolster offers digital risk protection that detects, monitors, and takes down phishing and fraudulent sites in real-time. Crooks can bypass restrictions to execute various cyberattacks.
Analysts from the Anti-Phishing Working Group (APWG) recorded 1,097,811 total phishing attacks in the second quarter of 2022 alone, a new record and the worst quarter for phishing APWG has ever observed. To do so, press Ctrl+F to open a Search window. This Tool is made for educational purpose only ! document.getElementById( "ak_js_1" ).setAttribute( "value", ( new Date() ).getTime() ); Copyright 2023 HackingLoops All Rights Reserved, Why These Are The Best Access Control Certifications, GPP cPassword Attack The tale of leaked key, Ethical Hacking Practice Test 6 Footprinting Fundamentals Level1, CEH Practice Test 5 Footprinting Fundamentals Level 0. WebThe phishing email is the lure of your PhishingBox template.
In this blog, we'll outline how to create a phishing website. Infosec IQ. People often overlook the senders address and delve straight into the content. Plus, the script we used works like a charm there! Phishing Domains, urls websites and threats database. Another Python tool created by Adam Compton. A final note I understand the guilt and shame of being scammed. Domain name permutation engine written in Go, A heavily armed customizable phishing tool for educational purpose only. Lets say youre working for a client, and youve been contracted to assess how security-aware their employees are. Locate the login page. PROFESSIONAL TOOL ORIENTED IN THE RECREATION OF PHISHING WEBSITE SCENARIOS, git clone https://github.com/AngelSecurityTeam/Recreator-Phishing, git clone https://github.com/AngelSecurityTeam/Recreator-Phishing.
Fraud occurs when a person, automated script, computer program or an auto clicker imitates a legitimate user of a web browser, clicking As you can see, both the email address and the password were logged. However, phishing sites arent all created equal. Lets say youre working for a client, and youve been contracted to assess how security-aware their employees are. Thats a situation where you can set up a phishing site that automatically logs their credentials to, say, an intranet website that they host. You signed in with another tab or window. Social Engineering Toolkit (SET) by Sensepost is a great example of Python based phishing tools. This is important, since most other tutorials will only tell you to change the permissions to 777, without even explaining what that means.
Step 2. Review the web page. Now that the PHP script is ready, we need to upload it to somewhere we can store the credentials we collect via our phishing page. Then, click on Select Files and navigate on the login_post.php file we created earlier. Each of our templates contains a phishing hook that will pull an unsuspecting target to your customized phishing landing page. Download the web page source. Step 5. Developed by TrustedSec, SpearPhisher says it all right in the description: A Simple Phishing Email Generation Tool. With an emphasis on simple. Designed for non-technical users, SpearPhisher is a Windows-based program with a straightforward GUI. So ALWAYS ask your client for permission before creating such phishing website. Security Awareness Training For Healthcare, how to host long-standing phishing infrastructure, PO Box 11163, Centenary Heights, QLD 4350, Australia. Note: Want more than just a phishing simulator? Advanced language models (such as GPT-3.5 and GPT-4) can produce hundreds of coherent, convincing phishing emails within minutes. Confirm that the web page loads. gets you full access to the PhishSim template library and education tools, but youll need to speak with an Infosec IQ representative for the ability to launch a free PhishSim campaign. topic page so that developers can more easily learn about it. WebTo do so, go back to the previous tab and hover on top of the section that corresponds to your site. Once the file with our malicious script has uploaded successfully, we need to change its permissions so that all users can read it, write to it, and run (execute) it. Youll notice the website looks exactly like the Facebook login page; except, of course, for the URL.
Programed by The Famous Sensei. WebYou can segment your audience based on multiple criteria, such as demographics, behaviors, and past interactions.
The PhishingBox Template Editor allows for you to dress the email to your liking to reel in targets.
WebOperation Huyao is a phishing attack that targets online shoppers without having to create a copy of the legitimate website.
Do I misinterpret the results, or are my parameters the cause of this problem? Just about every service we use has an internet-based component to it, this include social media, financial services, collaboration platforms and the list goes on. Support | The program has been in Beta since 2013, so its not likely to see any updates in the near future. Machine learning to classify Malicious (Spam)/Benign URL's. You also have to select a server of your choice and can make a legitimate-looking phishing URL or you can go with the random URL. https://bit.ly/3bWNfzK:00:00 - Introduction00:50 - What is phishing01:17 - SocialFish Setup guide04:50 - Cloning a page for #Phishing09:00 - Phishing over the Internet or WAN10:00 - PortMap Configuration15:01 - EndnoteSocialFish Commands executed in the Kali Linux terminal: ://.//. - - . . Follow Irfan on:https://twitter.com/irfaanshakeelhttps://facebook.com/mrirfanshakeel phishing-pages WebThese fake websites are used solely to steal your information. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. the URL which you want the user to be redirected to after performing a successful phishing attack.



